
|
Jupyter at Bryn Mawr College |
|
|
| Public notebooks: /services/public/dblank / CS240 Computer Organization / 2017-Fall / Notebooks | |||
5.4.5 The JMP Instruction¶
The conditional branch instruction, for all its capability, does have one unfortunate limitation. The next instruction executed must be within the range of addresses that can be computed by adding the incremented PC to the sign-extended offset obtained from bits [8:0] of the instruction. Since bits [8:0] specify a 2's complement integer, the next instruction executed after the conditional branch can be at most +256 or —255 locations from the branch instruction itself. What if we would like to execute next an instruction that is 1,000 locations from the current instruction. We cannot fit the value 1,000 into the 9-bit field; ergo, the conditional branch instruction does not work.
The LC-3 ISA does provide an instruction JMP (opcode = 1100) that can do the job. An example follows:
| 15 14 13 12 | 11 10 9 | 8 7 6 | 5 4 3 2 1 0 |
|---|---|---|---|
| 1 1 0 0 | 0 0 0 | 0 1 0 | 0 0 0 0 0 0 |
| JMP | R2 |
The JMP instruction loads the PC with the contents of the register specified by bits [8:6] of the instruction. If this JMP instruction is located at address x4000, R2 contains the value x6600, and the PC contains x4000, then the instruction at x4000 (the JMP instruction) will be executed, followed by the instruction located at x6600. Since registers contain 16 bits, the full address space of memory, the JMP instruction has no limitation on where the next instruction to be executed must reside.
The message is this: If a value in a register will be needed after something else is stored in that register, we must save it before the something else happens and restore it before we can subsequently use it. We save a register value by storing it in memory; we restore it by loading it back into the register.
The save/restore problem can be handled either by the initiating program before the TRAP occurs or by the called program (for example, the service routine) after the TRAP instruction executes. We will see in Section 9.2 that the same problem exists for another class of calling/called programs, the subroutine mechanism.
We use the term caller-save if the calling program handles the problem. We use the term callee-save if the called program handles the problem. The appropriate one to handle the problem is the one that knows which registers will be destroyed by subsequent actions.
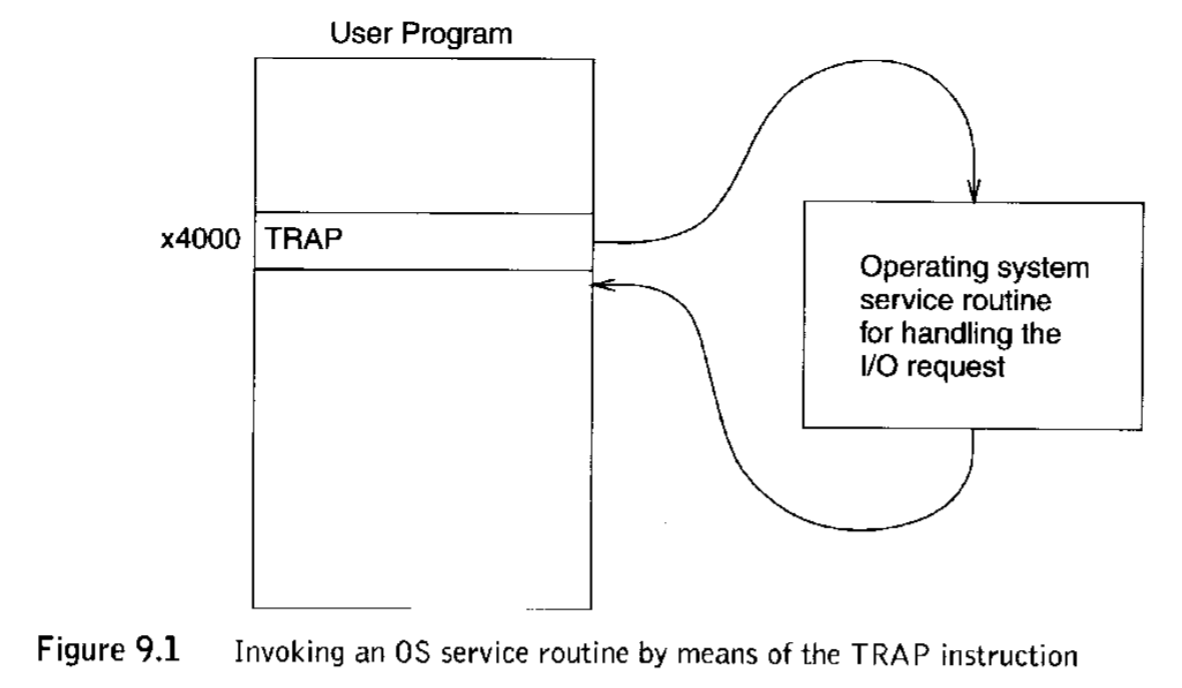
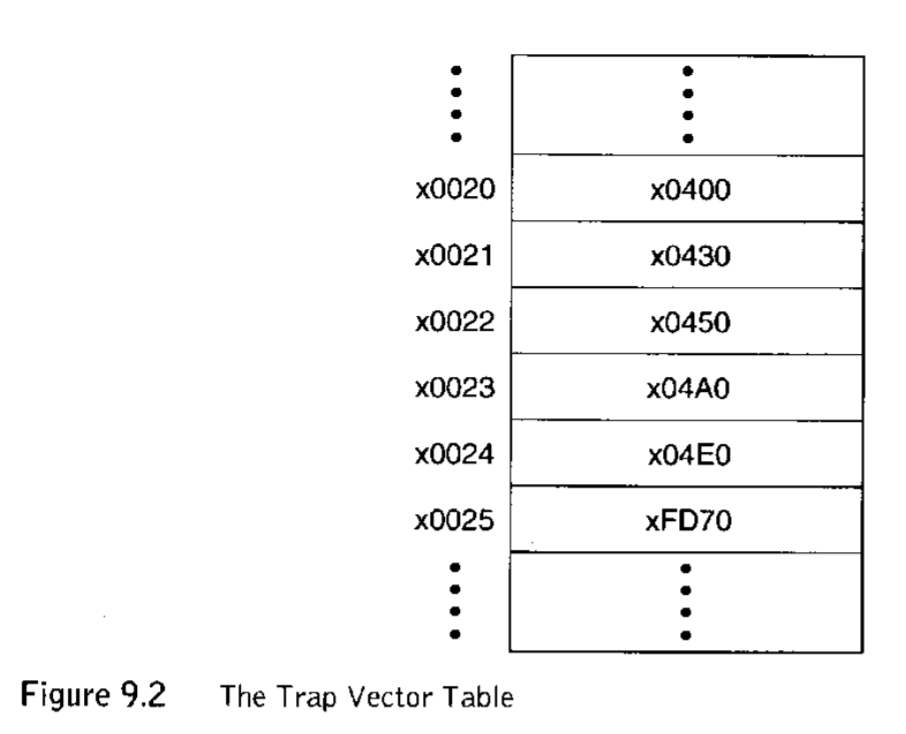
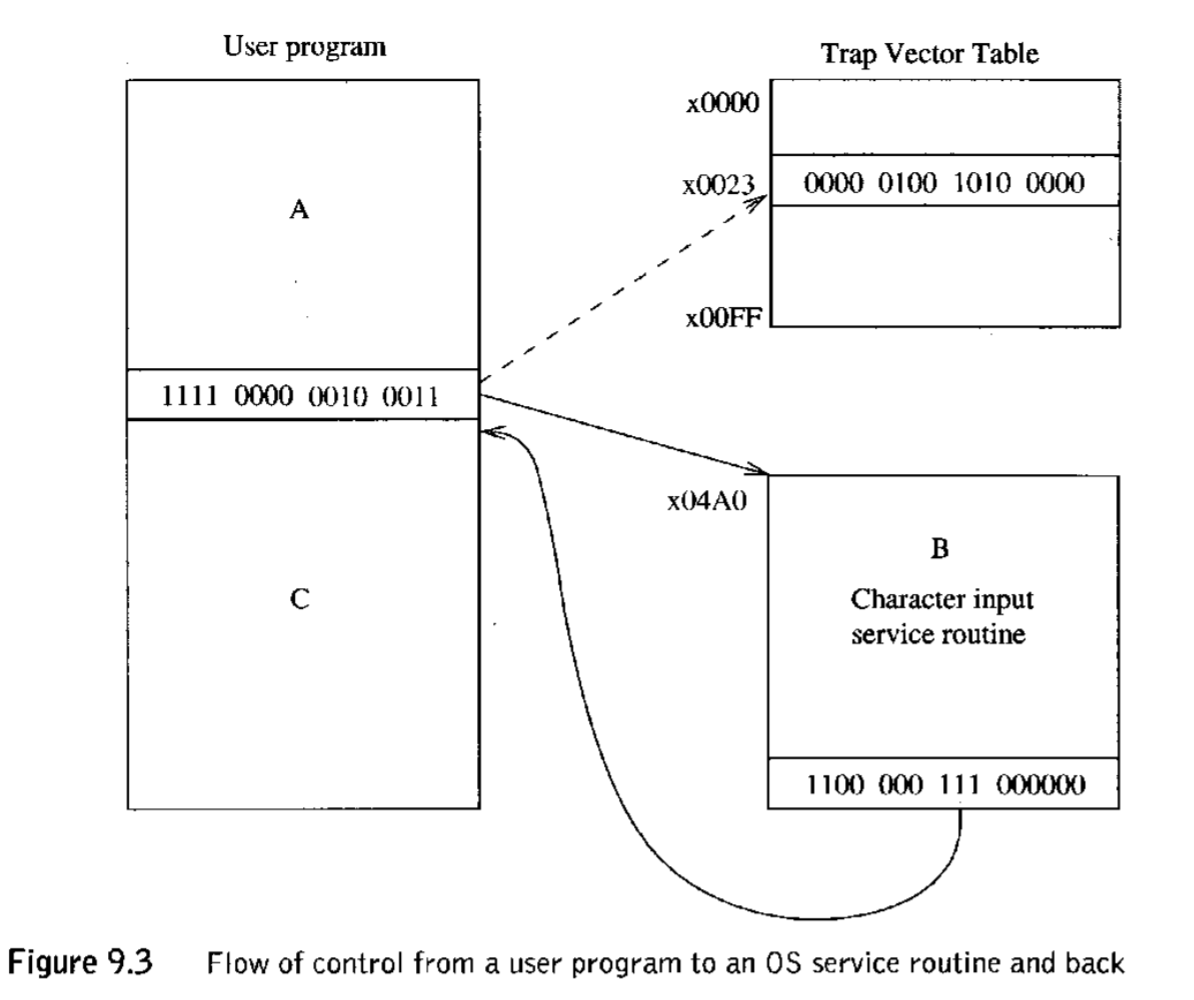
9.2 Subroutines¶
Sidebar: TRAP routines are only slightly different from subroutines. TRAP routines deal with permission to restricted hardware, such as a monitor, keyboard, etc. We won't dive any further into this privilege in this course. Take Operating Systems for further information on that topic.
Also, one might require a fragment that has been supplied by the manufacturer or by some independent software supplier. It is almost always the case that collections of such fragments are available to user programmers to free them from having to write their own. These collections are referred to as libraries. An example is the Math Library, which consists of fragments that execute such functions as square root, sine, and arctangent.
For all of these reasons, it is good to have a way to use program fragments efficiently. Such program fragments are called subroutines, or alternatively, procedures, or in C terminology, functions. The mechanism for using them is referred to as a Call/Return mechanism.
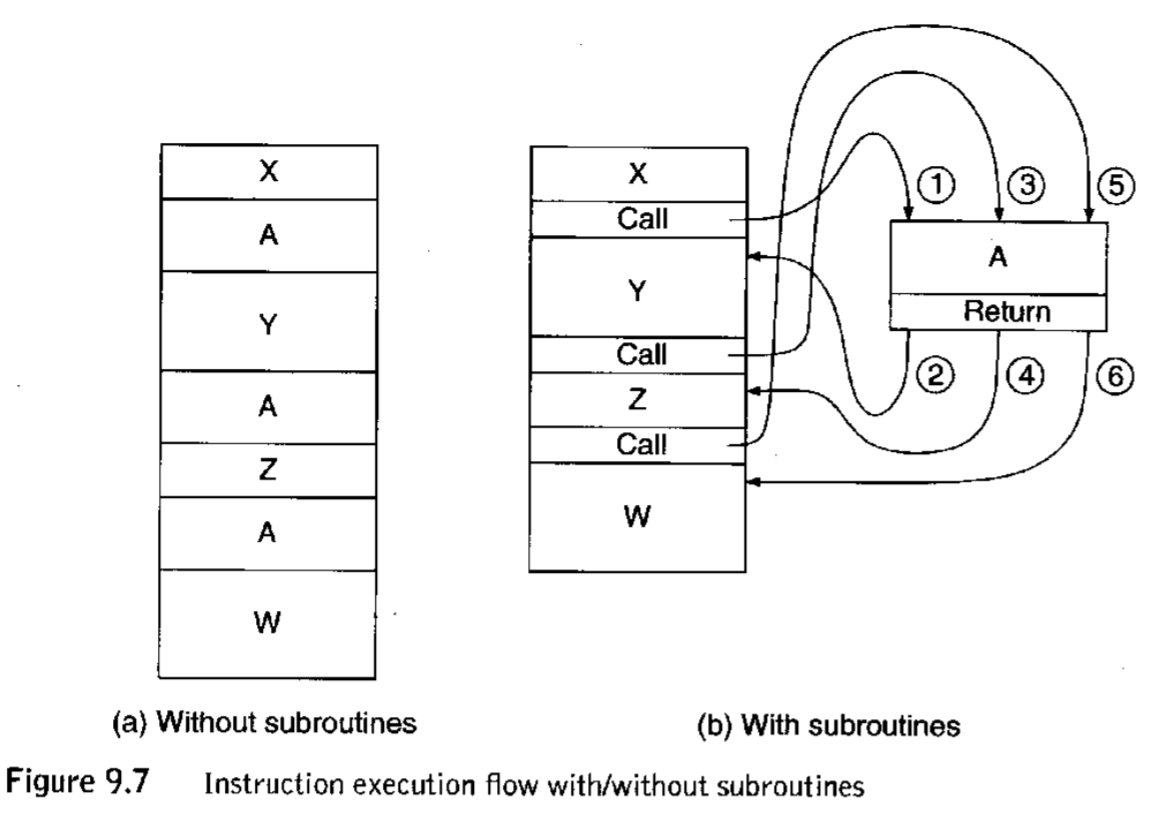
9.2.2 JSR/JSRR¶
| Opcode | Mode Flag | Operands |
|---|---|---|
| 0100 | 1 | PC offset11 |
| 0100 | 0 | 00 REG 000000 |
Modes:
- 1 - PC + offset is location of subroutine
- 0 - REG is location of subroutine